The Future of Passwordless
Last month, Internet celebrated the World Password Day. I saw a lot of posts about creating strong passwords, adopting MFA, and going Passwordless. In the same week, the FIDO alliance proposed enhancements to the WebAuthn specifications. And, last week Apple announced the general availability of PassKeys in WWDC. I am very excited about these innovations and wanted to reflect on my thoughts on why is it taking so long for us to get rid of passwords and the future of passwordless authentication.
Quick history on Passwords
Passwords have been there for over 60 years now. And we continue to heavily rely on passwords to protect our information including the sensitive ones such as our financial, banking, and health care information. Password managers can be really effective for managing your credentials. They help in creating strong unique passwords for every website. I did a quick check and I have about 320 unique passwords in my password vault. Despite the fact password managers have existed for a long time now, the adoption of password managers is extremely low even today. I know many of my friends who do not use password managers. To make things worse, the majority of internet users reuse the same passwords because it’s convenient and many lack awareness about the potential impact the reuse could cause. According to haveibeenawned.com, over 11 billion accounts have been compromised to date, most of which are due to weaker or reuse of passwords. The reason passwords are still continued to be used as the primary source of authentication is because of the seamless user experience it provides to the end-users. We are so used to typing in the username and password to a simple form and clicking the log-in button to sign in to a website. We might be wondering how am I able to sign in to some mobile apps just using the device biometrics(fingerprint or facial recognition)? These mobile apps baically cache the password on the device and use the biometrics to autofill your password. The weakest link here is still the password.
Multi-Factor Authentication
In order to mitigate the password problems, multi factor authentication came into existence where in I could use a second factor in addition to the password for authentication. MFAs have evolved over time. I still remember in my first job after I graduated, I was given an RSA hardware token that I need to use to access my workplace applications. These hardware tokens displayed a constantly changing code which I used as a second factor. I would have to carry the hardware tokens everywhere. After smartphone proliferation, I have used a number of software-based tokens i.e TOTPs such as Okta Verify, Google authenticator, and Authy as the second factor. For some consumer-based applications, I use SMS or Email based OTPs as a second factor depending on whatever the website offers. But email and SMS-based factors are highly prone to phishing. While MFA definitely offers a higher level of assurance compared to passwords, the penetration amongst the mainstream internet users and consumer applications are extremely low compared to enterprise adoption. There are about 5 billion internet users and millions of applications around the world. MFA adds additional friction to sign up, log in, and checkout flows which impacts end-user experience as well as user retention/conversion rates for these consumer applications.
FIDO2 and WebAuthn standard
In 2016, the FIDO Alliance came up with the WebAuthn standard. WebAuthn is a set of browser-based APIs that allows web applications to adopt public/private key pair-based credentials for authentication. If you are interested to learn more, I recommend reading the official specification. To keep it concise for this post, I am going to grossly simplify the standard. Public key cryptography is the same technology we use every time we access an HTTPS application. During a WebAuthn-based factor enrollment, the private key is stored securely on a client that the user owns i.e phone or a laptop and only the public key is shared with the respective application. Each of these public-private key pairs is unique to the application. The private keys are then protected using on-device biometrics such as fingerprint or facial recognition. Whenever I want to login into an application using WebAuthn, it will prompt me to use the on-device biometric and that’s it I am logged in to the application.
WebAuthn offers a high level of assurance due to the combination of public-key cryptography and on-device biometrics. Okay, so far WebAuthn is highly secure compared to passwords and SMS/Email-based logins, and they offer a seamless user experience - all I need to do is use the on-device biometrics. Then why have we not seen this replace passwords and become the primary authentication for consumer applications? Let me explain from my own experience.
Before the Pandemic, I traveled to India every year. When I returned back to the United States there is always a crazy long line for immigration. In 2019, I decided to enroll for Global entry in the hope that it would speed up the immigration process and I could return back home as soon as possible. And after 2019, Just like most of us, I have never made a single international trip as I publish this blog. That’s a story for another day. So I signed up for an online account to complete the application. During the enrollment, I was asked to enroll for two factors, password and something else. I was very excited to see WebAuthn-based biometrics as an option, so I decided to enroll in that.
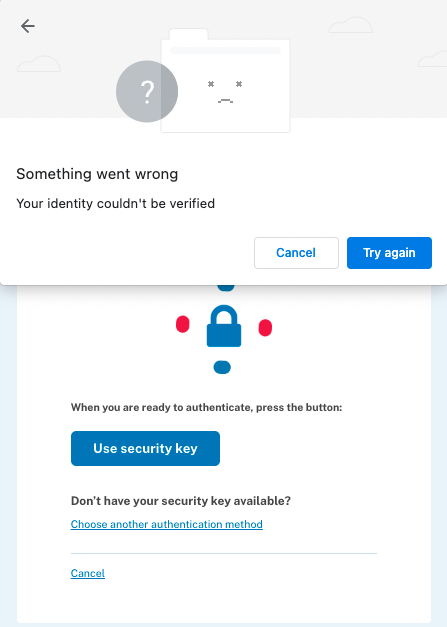
Everything was totally fine during the course of my application process for the next week. I opened my laptop, visited the website, used password as the first factor and fingerprint as the second factor and I was logged in. Around the same time, I bought a new laptop and configured it to be my daily driver. I wanted to complete the Global entry application that I started, so I tried logging into the website. When I tried to verify the second-factor using device biometrics, I got an error that my identity couldn’t be verified. The biometrics stopped working after I switched my laptop. Since then, I had to fall back on SMS-based OTP for the second factor.
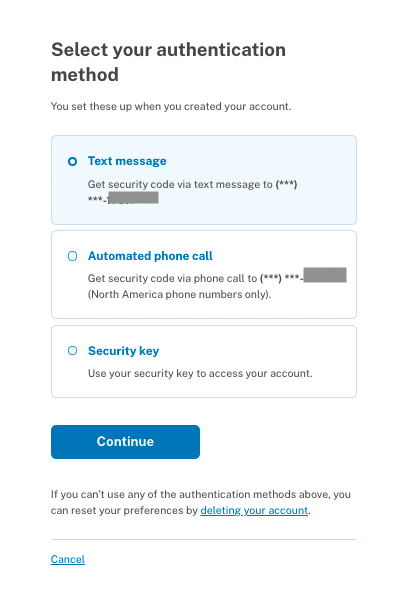
Limitations of WebAuthn
- As I mentioned earlier, The public-private key pairs are specific to an application (example: ttp.dhs.gov), and it is bound to the device. If I have to access the same website from my smartphone, I need to re-enroll for another set of keys to use WebAuthn on my phone. These multiple enrollments create such a pain for end-users.
- The account recovery process is equally painful. When I switched to the new laptop, I lost the private key along with my old laptop. That means I will no longer be able to log in to the website unless I have enrolled for an additional, less secure factor or I have another device where I have accessed the site before, say a smartphone. One other option available to the end users are to store these private keys in a separate hardware security key and carry it everywhere. This is so inconvinient and takes us back to the hardware tokens era.
In spite of offering a strong level of assurance, WebAuthn was never really able to make a dent on our over reliance on passwords. The adoption in the mainstream consumer space has been almost zero due to these limitations. This is all about to change.
WebAuthn Level 3 specification, Passkeys and a Passwordless future
The FIDO alliance and WebAuthn working group has come up with new enhancements to address the user experience gaps of WebAuthn which has the potential to offer a true passwordless and highly secure login option for everyone.
- The standards organization has been working with platform authentication vendors such as Apple, Google, and Microsoft to support the ability to use the same set of key pairs across multiple devices for an application. PassKeys are Apple’s implementation of this multi-device FIDO credentials standard. What’s so cool about sharing keys is that, once I enroll for biometric credentials on a website, say, when I log in via my MacBook, Apple can sync the keys across all the Apple devices. When I visit the same website through my iPhone, the keys are already available for me and I do not have to enroll again. All I have to do is use my FaceID upon the prompt and just log in to the website. This avoids multiple enrollment issues, and offers an easy account recovery if I lose my devices.
- Ok, What if I own an Android phone and a MacBook? As far as I know, Apple will sync these keys only across thier own devices. To address the cross-platform device problem, the FIDO alliance is proposing smartphones be used as Roaming authenticators. So instead of using a dedicated hardware security key, I could use my phone as the authenticator and share the keys between devices using Bluetooth. Let’s say I have already enrolled for WebAuthn credentials on a website using my phone and I am trying to log in to the same website on my MacBook. When I visit the website on my laptop, the browser will show me a QR code. All I need to do is connect my phone to my laptop via Bluetooth and scan the QR code. That’s it, I should be able to log in to the website.
I am very excited about these proposed standards as they will greatly reduce the trade-offs between security versus usability considerations. There will be some challenges along the way as this gets rolled out across all platforms and for every one of us to get used to it. But I truly think this will make Passwordless a viable and the most popular authentication method in the near future.